Synapse SSO service
The Synapse Matrix homeserver can be configured to use an OpenID Connect Provider (OP) for authentication, in addition to (or instead of) its own local password database.
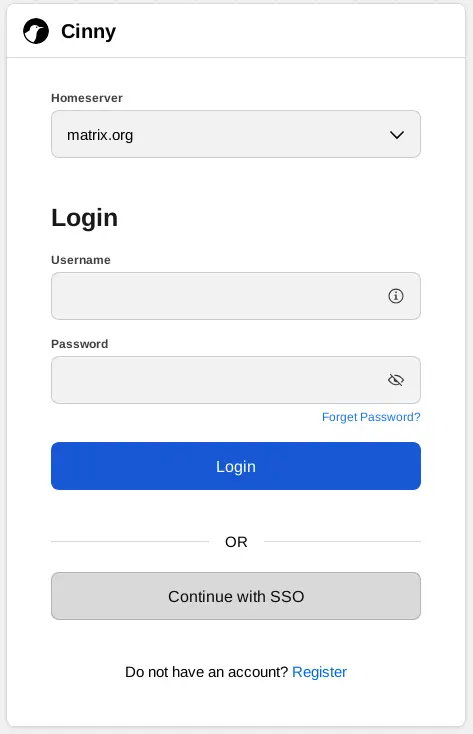
When Single Sign-On is enabled, Matrix client applications (like Cinny and Element) will provide a Continue with SSO button as shown in the screenshot below:
Getting started¶
⚠️ WARNING: Synapse SSO is supported by all major client apps, except for Element X. The developers of the Element X client apps made a deliberate choice to not support stable SSO implementation, focusing only on the new OIDC proposal (“next-gen auth”) instead.
This means that Synapse SSO does not work with Element X yet.
Any OpenID Connect Provider should work with Synapse, as long as it supports the authorization code flow. Frequent choices are Keycloak, Google and Github, but at least 15 other providers are known to work well.
To figure out how to prepare your OpenID Connect Provider and what configuration you would need, see the Sample Configs section of the Synapse documentation.
For new orders, you can provide the Synapse Single Sign-On details using dedicated fields in our order form - no YAML formatting required.
For adding SSO to existing servers, contact us and ideally send over a YAML configuration based on the sample config.
Operation¶
When at least one Single Sign-On provider is configured, Matrix client apps will start showing additional sign-in buttons (e.g. Continue with Keycloak).
By default, Synapse allows authentication both with its local password database and with the configured Single Sign-On providers. If you’d like to disable Synapse’s local database authentication and only rely on SSO, let us know and we’ll adjust the configuration for your server!
Multiple Single Sign-On providers can be enabled at the same time. Our order form only supports one, but feel free to contact us and we can enable any number of them!
Power up with Synapse SSO
Start using Synapse SSO today - get a managed Matrix server with it pre-installed, or add it to your existing setup.